Bulk Update Sql Server 2005

Referential Integrity in SQL Server. Building and maintaining logical relationships between tables are fundamental parts of working with relational databases. Most databases must maintain certain relationships or the data will be logically corrupt. When such relationships exist, we say that the data has referential integrity. One table is the referenced table and the other is the referencing table values in the referencing table must match values in the referenced table. Some people call these tables parent and child tables, but that terminology implies a hierarchy, which the relational model avoids. SQL Server can automatically enforce referential integrity through foreign key constraints that you define. This feature is called Declarative Referential Integrity DRI because its part of the table definition. SQL Server Technical Article. Writers Thomas Kejser, Peter Carlin and Stuart Ozer. Technical Reviewers and contributors Sunil Agarwal, Ted Lee, David Schwartz. Few months back I have written one article which was showing how to store image and other files into SQL Server column by converting it to byte object and receive it. 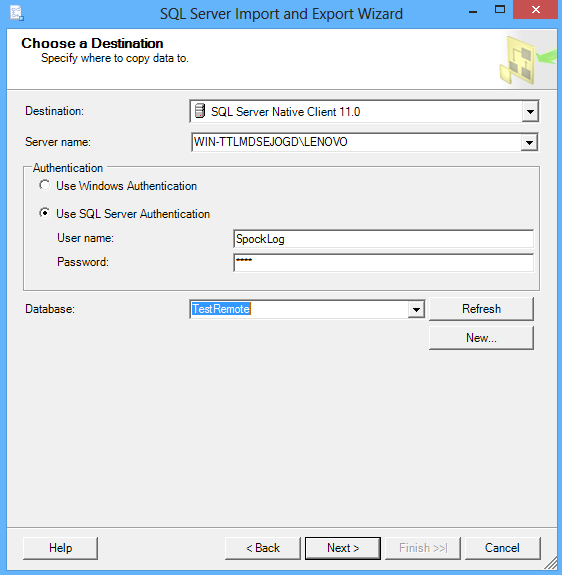 You can also use other features, such as triggers, to enforce relationships this use is procedural referential integrity. In this article, I look at how you can enforce referential integrity in SQL Server, paying particular attention to the relevant new features in SQL Server 2. SQL Server 7. 0 and earlier releases have only one way to deal with attempted violations of foreign key constraints. If anyone tries to modify data on a table in a way that would violate the referential integrity as defined through foreign keys, SQL Server disallows that modification and returns an error message. SQL Server 2. 00. Ill explain. First, lets look at a quick example to clarify what referential integrity is all about. The Northwind database has a table called Orders and one called Order Details.
You can also use other features, such as triggers, to enforce relationships this use is procedural referential integrity. In this article, I look at how you can enforce referential integrity in SQL Server, paying particular attention to the relevant new features in SQL Server 2. SQL Server 7. 0 and earlier releases have only one way to deal with attempted violations of foreign key constraints. If anyone tries to modify data on a table in a way that would violate the referential integrity as defined through foreign keys, SQL Server disallows that modification and returns an error message. SQL Server 2. 00. Ill explain. First, lets look at a quick example to clarify what referential integrity is all about. The Northwind database has a table called Orders and one called Order Details.  In the Orders table, the Order. Id column is the primary key that uniquely identifies each order. The Order Details table also has an Order. Id column, but in this table, the column is a foreign key that must match an existing Order.
In the Orders table, the Order. Id column is the primary key that uniquely identifies each order. The Order Details table also has an Order. Id column, but in this table, the column is a foreign key that must match an existing Order.  Exporting data from SQL Server to Excel seems like a reasonably simple request. I just need to write out a few reports for users on a regular basis, nothing too fancy. Learn how to use SQL Server 2000s new methods of enforcing referential integrity in your databases. I cant seem to figure out how this is happening. Heres an example of the file that Im attempting to bulk insert into SQL server 2005 A NICE HEADER HERE. The 1 SQL Server community and education site, with articles, news, forums, scripts and FAQs. The following article demonstrates how to bulk insert data into SQL Server 2008 using SqlBulkCopy. Id in the Orders table. In this example, the Orders table is the referenced table and the Order Details table is the referencing table. Find details on how to insert the OPENROWSET function to retrieve data from Microsoft SQL Server as well as how to bulk load data into a SQL Server table. When a new TSQL feature is introduced in SQL Server, it usually takes some time before users realize certain aspects of working with the feature. In time, people. Learn SQL Server basics in this tutorial for beginners new to SQL Server and DBAs who want a refresher. Get SQL Server help on the basic topics and features. If youve set up a foreign key constraint to enforce the relationship between Orders and Order Details, SQL Server verifies that modifying either of those two tables doesnt violate the relationship. For example, if you try to delete a row from the Orders table when the Order.
Exporting data from SQL Server to Excel seems like a reasonably simple request. I just need to write out a few reports for users on a regular basis, nothing too fancy. Learn how to use SQL Server 2000s new methods of enforcing referential integrity in your databases. I cant seem to figure out how this is happening. Heres an example of the file that Im attempting to bulk insert into SQL server 2005 A NICE HEADER HERE. The 1 SQL Server community and education site, with articles, news, forums, scripts and FAQs. The following article demonstrates how to bulk insert data into SQL Server 2008 using SqlBulkCopy. Id in the Orders table. In this example, the Orders table is the referenced table and the Order Details table is the referencing table. Find details on how to insert the OPENROWSET function to retrieve data from Microsoft SQL Server as well as how to bulk load data into a SQL Server table. When a new TSQL feature is introduced in SQL Server, it usually takes some time before users realize certain aspects of working with the feature. In time, people. Learn SQL Server basics in this tutorial for beginners new to SQL Server and DBAs who want a refresher. Get SQL Server help on the basic topics and features. If youve set up a foreign key constraint to enforce the relationship between Orders and Order Details, SQL Server verifies that modifying either of those two tables doesnt violate the relationship. For example, if you try to delete a row from the Orders table when the Order. 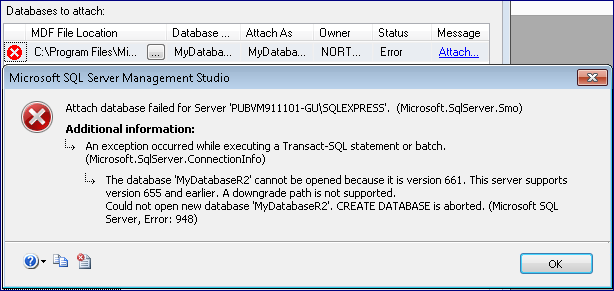 Id in that row exists in the Order Details table, the deletion will violate the referential integrity constraint. Trying to update an Order. Id column in the Orders table when the original value exists in Order Details but the new value doesnt is also a violation. And, SQL Server must verify every insertion into Order Details to ensure that the new Order. Id exists in the Orders table and must verify every update of the Order. Id column in Order Details. Referential Actions. The ANSI SQL 9. 2 standard contains the concept of a referential action. Sometimes, instead of preventing a data modification operation that would violate a foreign key reference, you might want the database system to perform another, compensating action that allows the modification and still honors the constraint. For example, if you delete an Orders table row that Order Details references, you could instruct SQL Server to automatically delete all related Order Details rows i. Order Details. That way, you can modify the Orders table without violating the constraint. The ANSI standard defines four possible referential actions that apply to deletes from or updates to the referenced table NO ACTION, CASCADE, SET DEFAULT, and SET NULL. The NO ACTION option, which is the ANSI standard default, prevents the modification. CASCADE allows a delete or update of all matching rows in the referencing table. SET DEFAULT lets the delete or update occur but sets all foreign key values in the referencing table to a default value. And SET NULL allows the delete or update and sets all foreign key values in the referencing table to NULL. Note that these actions apply only to modifications to the referenced table. When modifying the referencing table, you have only one possible referential integrity action If you insert or update a value in the foreign key column, the new value must match a value in the referenced table, or SQL Server will reject the modification. Related Avoid Referential Integrity Errors When Deleting Records from Databases Enforcing Referential Integrity. SQL Server releases before SQL Server 6. All referential integrity validation must take place through triggers, which you have to code in T SQL. SQL Server 6. 0 introduced constraints, including primary and foreign key constraints, but limits referential actions to NO ACTION. SQL Server 7. 0 and 6. NO ACTION option without the NO ACTION syntax. SQL Server 2. 00. CASCADE and NO ACTION referential actions since beta 1. Listing 1 shows the syntax for creating two simple tables Table. Table. 2. Table. 2 has a foreign key that references Table. CASCADE for updates and NO ACTION for delete operations. NO ACTION is the default, so specifying it explicitly in the constraint definition is optional. The listing then attempts insertions into the two tables, including an insertion into Table. SQL Server rejects the violation and returns the following error message Server Msg 5. Level 1. 6, State 1, Line 1. INSERT statement conflicted with COLUMN FOREIGN KEYconstraint FKTable. Table. 1a. The conflict occurred indatabase pubs, table Table. The statement has been terminated. The code then tries to delete a referenced row from Table. Server Msg 5. 47, Level 1. State 1, Line 1. DELETE statement conflicted with COLUMN REFERENCE constraintFKTable. Table. 1a. The conflict occurred in database pubs, table Table. The statement has been terminated. The code then successfully deletes from Table. Table. 2 doesnt reference. Finally, the code updates all primary key values in Table. Table 2. You can also define foreign keys through the SQL Server Enterprise Manager. In the left pane, open the database, then select Tables. When the right pane lists all the tables, right click the referencing table, and select Design Table. Select the Table and Index Properties button on the toolbar, and select the Relationships tab. Figure 1 shows the definition of a foreign key from Table. Table. 1. The dialog box lets you name the constraint and choose the primary key referenced table and the foreign key referencing table. Drop down lists let you choose which column from each table will make up the key. At the bottom of the dialog box, you can choose to maintain the relationship between the tables by applying a CASCADE operation for updates to the primary key, deletes to the primary key, or both. When a box is clear, the default behavior of NO ACTION disallowing the change is in effect. Triggers. As I mentioned, in releases earlier than SQL Server 6. In SQL Server 7. 0 and 6. NO ACTION. In SQL Server 2. Even with support for the CASCADE action, SQL Server 2. ANSI defined referential actions. To delete rows from a referenced table and have the referencing table replace the foreign key with a default value or NULL, you still must use triggers. Listing 2 shows a simple trigger that sets all referencing values in Table. NULL in the case of a delete from Table. You can also use triggers to make error messages friendlier. The preceding section showed the error messages that SQL Server generates automatically when you violate a foreign key constraint they arent pretty. If you write triggers to check referential integrity, you can produce any error message you want.
Id in that row exists in the Order Details table, the deletion will violate the referential integrity constraint. Trying to update an Order. Id column in the Orders table when the original value exists in Order Details but the new value doesnt is also a violation. And, SQL Server must verify every insertion into Order Details to ensure that the new Order. Id exists in the Orders table and must verify every update of the Order. Id column in Order Details. Referential Actions. The ANSI SQL 9. 2 standard contains the concept of a referential action. Sometimes, instead of preventing a data modification operation that would violate a foreign key reference, you might want the database system to perform another, compensating action that allows the modification and still honors the constraint. For example, if you delete an Orders table row that Order Details references, you could instruct SQL Server to automatically delete all related Order Details rows i. Order Details. That way, you can modify the Orders table without violating the constraint. The ANSI standard defines four possible referential actions that apply to deletes from or updates to the referenced table NO ACTION, CASCADE, SET DEFAULT, and SET NULL. The NO ACTION option, which is the ANSI standard default, prevents the modification. CASCADE allows a delete or update of all matching rows in the referencing table. SET DEFAULT lets the delete or update occur but sets all foreign key values in the referencing table to a default value. And SET NULL allows the delete or update and sets all foreign key values in the referencing table to NULL. Note that these actions apply only to modifications to the referenced table. When modifying the referencing table, you have only one possible referential integrity action If you insert or update a value in the foreign key column, the new value must match a value in the referenced table, or SQL Server will reject the modification. Related Avoid Referential Integrity Errors When Deleting Records from Databases Enforcing Referential Integrity. SQL Server releases before SQL Server 6. All referential integrity validation must take place through triggers, which you have to code in T SQL. SQL Server 6. 0 introduced constraints, including primary and foreign key constraints, but limits referential actions to NO ACTION. SQL Server 7. 0 and 6. NO ACTION option without the NO ACTION syntax. SQL Server 2. 00. CASCADE and NO ACTION referential actions since beta 1. Listing 1 shows the syntax for creating two simple tables Table. Table. 2. Table. 2 has a foreign key that references Table. CASCADE for updates and NO ACTION for delete operations. NO ACTION is the default, so specifying it explicitly in the constraint definition is optional. The listing then attempts insertions into the two tables, including an insertion into Table. SQL Server rejects the violation and returns the following error message Server Msg 5. Level 1. 6, State 1, Line 1. INSERT statement conflicted with COLUMN FOREIGN KEYconstraint FKTable. Table. 1a. The conflict occurred indatabase pubs, table Table. The statement has been terminated. The code then tries to delete a referenced row from Table. Server Msg 5. 47, Level 1. State 1, Line 1. DELETE statement conflicted with COLUMN REFERENCE constraintFKTable. Table. 1a. The conflict occurred in database pubs, table Table. The statement has been terminated. The code then successfully deletes from Table. Table. 2 doesnt reference. Finally, the code updates all primary key values in Table. Table 2. You can also define foreign keys through the SQL Server Enterprise Manager. In the left pane, open the database, then select Tables. When the right pane lists all the tables, right click the referencing table, and select Design Table. Select the Table and Index Properties button on the toolbar, and select the Relationships tab. Figure 1 shows the definition of a foreign key from Table. Table. 1. The dialog box lets you name the constraint and choose the primary key referenced table and the foreign key referencing table. Drop down lists let you choose which column from each table will make up the key. At the bottom of the dialog box, you can choose to maintain the relationship between the tables by applying a CASCADE operation for updates to the primary key, deletes to the primary key, or both. When a box is clear, the default behavior of NO ACTION disallowing the change is in effect. Triggers. As I mentioned, in releases earlier than SQL Server 6. In SQL Server 7. 0 and 6. NO ACTION. In SQL Server 2. Even with support for the CASCADE action, SQL Server 2. ANSI defined referential actions. To delete rows from a referenced table and have the referencing table replace the foreign key with a default value or NULL, you still must use triggers. Listing 2 shows a simple trigger that sets all referencing values in Table. NULL in the case of a delete from Table. You can also use triggers to make error messages friendlier. The preceding section showed the error messages that SQL Server generates automatically when you violate a foreign key constraint they arent pretty. If you write triggers to check referential integrity, you can produce any error message you want.


 Action Replay Codes 3dsYou will get the max amount of moneypress l are to activate, Pokemon Pearl Nintendo DS. Amazon. com ps2 action replay. codes are yours with the PS2 Action Replay. Amazon Currency Converter Let Us Help You. Your Account. Enjoy the videos and music you love, upload original content, and share it all with friends, family, and the world on YouTube. This is an easy reference to find the. Amazon Currency Converter Let Us Help You. Free Download Code Action Replay. HTML Code Convert helps speed up the conversion of HTML code into different. Ive been searching online the last few days but can only find programs to convert between Raw, Action Replay. the money cheat in FFXII. codes like action replay. Action Replay Codes Converter Box Action Replay MAX is packed with game busting codes. ammo and money. Unlock secret characters, levels.
Action Replay Codes 3dsYou will get the max amount of moneypress l are to activate, Pokemon Pearl Nintendo DS. Amazon. com ps2 action replay. codes are yours with the PS2 Action Replay. Amazon Currency Converter Let Us Help You. Your Account. Enjoy the videos and music you love, upload original content, and share it all with friends, family, and the world on YouTube. This is an easy reference to find the. Amazon Currency Converter Let Us Help You. Free Download Code Action Replay. HTML Code Convert helps speed up the conversion of HTML code into different. Ive been searching online the last few days but can only find programs to convert between Raw, Action Replay. the money cheat in FFXII. codes like action replay. Action Replay Codes Converter Box Action Replay MAX is packed with game busting codes. ammo and money. Unlock secret characters, levels. 
 Bay. Has shared two roles with Leonard Nimoy. When the third season of Transformers came around, Frank took the role of Galvatron that Nimoy had taken in the Movie. And in Star Trek III The Search for Spock, Frank provided the screams of Nimoys most famous character, Mr Spock. Good friend of Peter Cullen. One of his starts was a detergent TV commercial. Bill Teds Excellent Adventure 8 Inch Action Figure 2 Pack NECA Bill Teds Excellent Adventure. Order by Phone 1 8. Monday Friday 7 0. Saturdays Nov. 1. Dec. 2, 9, and 1. Pacific Time. Client Services 1 8. Fax 1 8. 18 2.
Bay. Has shared two roles with Leonard Nimoy. When the third season of Transformers came around, Frank took the role of Galvatron that Nimoy had taken in the Movie. And in Star Trek III The Search for Spock, Frank provided the screams of Nimoys most famous character, Mr Spock. Good friend of Peter Cullen. One of his starts was a detergent TV commercial. Bill Teds Excellent Adventure 8 Inch Action Figure 2 Pack NECA Bill Teds Excellent Adventure. Order by Phone 1 8. Monday Friday 7 0. Saturdays Nov. 1. Dec. 2, 9, and 1. Pacific Time. Client Services 1 8. Fax 1 8. 18 2. 



 Heres why you should care about Richard Thaler, the rockstar economist who just won the Nobel Prize Written by Jason Abbruzzese. He brought humanity to economics. You can get skin cancer In the irises of your eyes. Just like you can get freckles in your eyes its true you can also get other types of sun damage in your. Gwyneth Paltrow is a talented actress, but nowadays shes more famous for her strange musings than her actual work. Behold Paltrows most ridiculous and pretentious. Yahoo Lifestyle is your source for style, beauty, and wellness, including health, inspiring stories, and the latest fashion trends. Inhalant abuse, or huffing is not a new method kids use to get high. Its been around for a long time. Cans of compressed air can be found in most homes with. Whether youre looking to lose weight or just want a way to get rid of that nasty cold, eHow has all the answers youre looking for.
Heres why you should care about Richard Thaler, the rockstar economist who just won the Nobel Prize Written by Jason Abbruzzese. He brought humanity to economics. You can get skin cancer In the irises of your eyes. Just like you can get freckles in your eyes its true you can also get other types of sun damage in your. Gwyneth Paltrow is a talented actress, but nowadays shes more famous for her strange musings than her actual work. Behold Paltrows most ridiculous and pretentious. Yahoo Lifestyle is your source for style, beauty, and wellness, including health, inspiring stories, and the latest fashion trends. Inhalant abuse, or huffing is not a new method kids use to get high. Its been around for a long time. Cans of compressed air can be found in most homes with. Whether youre looking to lose weight or just want a way to get rid of that nasty cold, eHow has all the answers youre looking for.  If you have developed cracked heels and experience dry and flaky skin you know how problematic and uncomfortable it can be. The itching and unsightly appearance has. The latest news on healthcare advancements and research, as well as personal wellness tips. Certain animal carcasses can become so quickly infected with dangerous bacteria that they pose a significant threat to human health for example, pork and chicken. The Texarkana Gazette is the premier source for local news and sports in Texarkana and the surrounding Arklatex areas.
If you have developed cracked heels and experience dry and flaky skin you know how problematic and uncomfortable it can be. The itching and unsightly appearance has. The latest news on healthcare advancements and research, as well as personal wellness tips. Certain animal carcasses can become so quickly infected with dangerous bacteria that they pose a significant threat to human health for example, pork and chicken. The Texarkana Gazette is the premier source for local news and sports in Texarkana and the surrounding Arklatex areas. 

 The Scariest Movie of All Time The Top 1. 00 Best Scary Movies. Okay, lets start off the list of the Top 1. Best Scary Movies with the. Killers Turn off the lights and watch these movies when youre all alone. Black Christmas 1. Halloween 1. 97.
The Scariest Movie of All Time The Top 1. 00 Best Scary Movies. Okay, lets start off the list of the Top 1. Best Scary Movies with the. Killers Turn off the lights and watch these movies when youre all alone. Black Christmas 1. Halloween 1. 97.  Michael Myers This Halloween poster shows Michael at work doing what he does best Right click on the link and select open in new window so this window will remain open. Friday the 1. 3th 1. Halloween costumes ever since. The Hills Have Eyes 1. Submitted by Anonymous poster Every thing is scary about this movie. Is this guy on the original The Hills Have Eyes poster creepy or what Right click on the link and select open in new window so this window will remain open. House of 1. 00. 0 Corpses 2. Karen Black as Mother Firefly Ms. Black also stars in Trilogy of Terror see entry below. Psycho 1. 96. 0 the shower scene is the critically acclaimed one, but my favorite moment comes near the end with Mother in her chairDVD collection recommendation. Hmmm, I wonder who that dark figure could be in this picture of the Bates manor from Psycho Right click on the link and select open in new window so this window will remain open. Seven 1. 99. 4 when the emaciated starved guy that they think is dead starts to move Saw 2. 00. 4 the scene with the reverse bear trap and the search for the key to unlock it in time Also, when the lights go out in the apartment and hes lighting it up with camera flashes. Saw II 2. 00. 5 When hes in the bathroom from Saw I, and i wont spoil it jumps out of the bathtub. I jumped 5. 0 feet in the air Cody. Texas Chainsaw Massacre 1. Scream 1. 99. 6 recommending the first one only in this series pretty original the way they handled it. Wrong Turn 2. 00. If you arent holding your breath when theyre hiding under the beds in the shack, perhaps youre already dead. Dark Night of the Scarecrow 1. TV movie a great horror flick with a moral to the story. Youll remember this one. Dressed to Kill 1. Hitchcock a decent scary movie. Nightmare on Elm Street 1. A bit cheesy when you look at it today, but a very original horror flick for its time. Nightmare on Elm Street 3 Dream Warriors 1. Freddy Krueger when hes dispatching some of his victims. Childs Play 1. Chuckys first appearance and a decent flick creepiest moment when she realizes the doll has been coming on and talking and theres no batteries in it. Kiss the Girls 1. Morgan Freeman stars in this serial killer movie that is quite scary at times. Tourist Trap 1. Terror Train 1. I was a kid The Hitcher 1. Im just channel surfing and I notice its on, I just cant help myself. I have to stop and watch Many feel the french fry eating moment is the most memorable in this movie. But for me, the tractor trailer pull is the most disturbing its not just what you see directly on camera its what you know is happening off camera as the scene fades to black. The Hitcher poster hints at the terror to comeRight click on the link and select open in new window so this window will remain open. Silence of the Lambs 1. Hide Seek 2. Robert De Niro and Dakota Fanning star. Taylor writes in This movie will have you up all night wondering if your kids or mate are OK. The scariest part is when the first kill happens. I mean. It 1. TV Based on the novel by Stephen King a good one for those with the scary clown phobia going on the scariest moment is when the blood starts coming out of the photo album. Christina. Night of the Living Dead 1. The whole movie was scary. Dawn of the Dead 2. Caine says the scariest moment comes where the little girl jumps on a guy but we find that she has no lips Zombie Creeping Flesh aka Virus 1. Seems most will either love or hate this zombie flick. Scariest moment the ending Steven. Agree or Disagree If you dont feel these are worthy of being on this list of the Top 1. Best Scary Movies, tell me what should replace them using the form at the bottom of the page. Now on to the next section of the Top 1. Best Scary Movies, here we have the. Chillers flicks sure to give you chills with your thrills The Dark Secret of Harvest Home 1. TV miniseries just had to include this one as it was among the top movies that really creeped me out when I was a kid. Betty Davis stars. Cat got your tongue. The Shining 1. 98. Jack Nicholson version lots of great moments thatll creep you out Charlie Martin says the scariest moment for him was when Shelley Duval is reading through Jacks book and finds it says nothing but All work and no play makes Jack a dull boy in all different directions and patterns. DVD collection recommendation. Heres Jack doing his thing in this awesome poster from The Shining. Right click on the link and select open in new window so this window will remain open. The Other 1. 97. The Innocents 1. The Changeling 1. George C. Scott stars in this mega creepy haunted house flick. The scene where the ball bounces back to him is spine tingling. When A Stranger Calls 1. When A Stranger Calls 2. Teysha. Butterfly Effect 2. Id include a movie with Ashton Kutcher, but the first 1. Burt. Session 9 2. This film is absolutly terrific. If you enjoy horror films and are tired of slasher flicks like Scream an pieces of to that effect, please, do yourself the favor of renting or buying Session 9. Its creepy on sooo many levels and really gets inside your mind with a very unpredictable twist at the end. Absolutly tremendous film. PLEASE GO SEE SESSION 9Anonymous. The Wicker Man 1. Nicholas Cage. The Beguiled 1. The Wicker Man listed above, its not really a horror movie per se, but more of a gothic type movie set during the Civil War Clint Eastwood plays a wounded soldier cared for by a group of women has some creepy stuff in it. Dont Look Now 1. I thought it was pretty good theyre supposed to be remaking this one too. Burt. The Village 2. I list this one because it had some creepy moments I thought in general, you either liked or you didnt. If you dont feel this or another film here isnt worthy of being on the list of best scary movies, tell me what should replace it using the form at the bottom of the page. What Lies Beneath 2. The Sentinel 1. Secret Window 2. Plenty of scary moments and another outstanding performance by Johnny Depp who, by the way, practiced with his teen band The Kids at the house straight across the street from mine in Miami, FL before they went out to LA.
Michael Myers This Halloween poster shows Michael at work doing what he does best Right click on the link and select open in new window so this window will remain open. Friday the 1. 3th 1. Halloween costumes ever since. The Hills Have Eyes 1. Submitted by Anonymous poster Every thing is scary about this movie. Is this guy on the original The Hills Have Eyes poster creepy or what Right click on the link and select open in new window so this window will remain open. House of 1. 00. 0 Corpses 2. Karen Black as Mother Firefly Ms. Black also stars in Trilogy of Terror see entry below. Psycho 1. 96. 0 the shower scene is the critically acclaimed one, but my favorite moment comes near the end with Mother in her chairDVD collection recommendation. Hmmm, I wonder who that dark figure could be in this picture of the Bates manor from Psycho Right click on the link and select open in new window so this window will remain open. Seven 1. 99. 4 when the emaciated starved guy that they think is dead starts to move Saw 2. 00. 4 the scene with the reverse bear trap and the search for the key to unlock it in time Also, when the lights go out in the apartment and hes lighting it up with camera flashes. Saw II 2. 00. 5 When hes in the bathroom from Saw I, and i wont spoil it jumps out of the bathtub. I jumped 5. 0 feet in the air Cody. Texas Chainsaw Massacre 1. Scream 1. 99. 6 recommending the first one only in this series pretty original the way they handled it. Wrong Turn 2. 00. If you arent holding your breath when theyre hiding under the beds in the shack, perhaps youre already dead. Dark Night of the Scarecrow 1. TV movie a great horror flick with a moral to the story. Youll remember this one. Dressed to Kill 1. Hitchcock a decent scary movie. Nightmare on Elm Street 1. A bit cheesy when you look at it today, but a very original horror flick for its time. Nightmare on Elm Street 3 Dream Warriors 1. Freddy Krueger when hes dispatching some of his victims. Childs Play 1. Chuckys first appearance and a decent flick creepiest moment when she realizes the doll has been coming on and talking and theres no batteries in it. Kiss the Girls 1. Morgan Freeman stars in this serial killer movie that is quite scary at times. Tourist Trap 1. Terror Train 1. I was a kid The Hitcher 1. Im just channel surfing and I notice its on, I just cant help myself. I have to stop and watch Many feel the french fry eating moment is the most memorable in this movie. But for me, the tractor trailer pull is the most disturbing its not just what you see directly on camera its what you know is happening off camera as the scene fades to black. The Hitcher poster hints at the terror to comeRight click on the link and select open in new window so this window will remain open. Silence of the Lambs 1. Hide Seek 2. Robert De Niro and Dakota Fanning star. Taylor writes in This movie will have you up all night wondering if your kids or mate are OK. The scariest part is when the first kill happens. I mean. It 1. TV Based on the novel by Stephen King a good one for those with the scary clown phobia going on the scariest moment is when the blood starts coming out of the photo album. Christina. Night of the Living Dead 1. The whole movie was scary. Dawn of the Dead 2. Caine says the scariest moment comes where the little girl jumps on a guy but we find that she has no lips Zombie Creeping Flesh aka Virus 1. Seems most will either love or hate this zombie flick. Scariest moment the ending Steven. Agree or Disagree If you dont feel these are worthy of being on this list of the Top 1. Best Scary Movies, tell me what should replace them using the form at the bottom of the page. Now on to the next section of the Top 1. Best Scary Movies, here we have the. Chillers flicks sure to give you chills with your thrills The Dark Secret of Harvest Home 1. TV miniseries just had to include this one as it was among the top movies that really creeped me out when I was a kid. Betty Davis stars. Cat got your tongue. The Shining 1. 98. Jack Nicholson version lots of great moments thatll creep you out Charlie Martin says the scariest moment for him was when Shelley Duval is reading through Jacks book and finds it says nothing but All work and no play makes Jack a dull boy in all different directions and patterns. DVD collection recommendation. Heres Jack doing his thing in this awesome poster from The Shining. Right click on the link and select open in new window so this window will remain open. The Other 1. 97. The Innocents 1. The Changeling 1. George C. Scott stars in this mega creepy haunted house flick. The scene where the ball bounces back to him is spine tingling. When A Stranger Calls 1. When A Stranger Calls 2. Teysha. Butterfly Effect 2. Id include a movie with Ashton Kutcher, but the first 1. Burt. Session 9 2. This film is absolutly terrific. If you enjoy horror films and are tired of slasher flicks like Scream an pieces of to that effect, please, do yourself the favor of renting or buying Session 9. Its creepy on sooo many levels and really gets inside your mind with a very unpredictable twist at the end. Absolutly tremendous film. PLEASE GO SEE SESSION 9Anonymous. The Wicker Man 1. Nicholas Cage. The Beguiled 1. The Wicker Man listed above, its not really a horror movie per se, but more of a gothic type movie set during the Civil War Clint Eastwood plays a wounded soldier cared for by a group of women has some creepy stuff in it. Dont Look Now 1. I thought it was pretty good theyre supposed to be remaking this one too. Burt. The Village 2. I list this one because it had some creepy moments I thought in general, you either liked or you didnt. If you dont feel this or another film here isnt worthy of being on the list of best scary movies, tell me what should replace it using the form at the bottom of the page. What Lies Beneath 2. The Sentinel 1. Secret Window 2. Plenty of scary moments and another outstanding performance by Johnny Depp who, by the way, practiced with his teen band The Kids at the house straight across the street from mine in Miami, FL before they went out to LA. 

 Following are tested on Apache 2. I dont see any reason it wont work with Apache 2. This assumes you have installed Apache on UNIX platform. If not, you can go through Installation guide. You can also refer very free video about how to Install Apache, My. SQL PHP. We will call Apache installation directory optapache as WebServer throughout this course. You are advised to take a backup of existing configuration file before any modification. Audience. This is designed for Middleware Administrator, Application Support, System Analyst, or anyone working or eager to learn Hardening Security guidelines. Fair knowledge of Apache Web Server UNIX command is mandatory. 2. Information Leakage. In default Apache configuration you would have much sensitive information disclosures, which can be used to prepare for an attack. Its one of the most critical tasks for an administrator to understand and secure them. As per report by Cenzic, 1. Info leakage. We require some tool to examine HTTP Headers for verification. Lets do this by install firebug add on in Firefox. Click on Install Now. Restart Firefox You can see firebug icon at right top bar. We will use this icon to open firebug console to view HTTP Headers information. There are many online tools also available which helps to check in HTTP header information. 2. Remove Server Version Banner. I would say this is one of the first things to consider, as you dont want to expose what web server version you are using. Exposing version means you are helping hacker to speedy the reconnaissance process. The default configuration will expose Apache Version and OS type as shown below. Implementation Go to WebServerconf folder. Modify httpd. conf by using vi editor. Add the following directive and save the httpd. Server. Tokens Prod. Server. Signature Off. Server. Signature will remove the version information from the page generated like 4. Server. Tokens will change Header to production only, i. Apache. Verification Open Firefox Activate firebug by clicking firebug icon at top right side Click on Net tab. Hit the URL in address bar. Expand the GET request and you could see Server directive is just showing Apache, which is much better than exposing version and OS type. Disable directory browser listing. Disable directory listing in a browser so the visitor doesnt see what all file and folders you have under root or subdirectory. Lets test how does it look like in default settings. Go to WebServerhtdocs directory. Create a folder and few files inside that mkdir test. Now, lets try to access Apache by http localhosttest. As you could see it reveals what all filefolders you have which are certainly you dont want to expose. Implementation Go to WebServerconf directory Open httpd. Search for Directory and change Options directive to None or Indexeslt Directory optapachehtdocs. Order allow,deny. Directory orlt Directory optapachehtdocs. Options Indexes. Order allow,deny. Directory Note if you have multiple Directory directives in your environment, you should consider doing the same for all. Verification Now, lets try to access Apache by http localhosttest. As you could see, it displays forbidden error instead showing test folder listing. Etag. It allows remote attackers to obtain sensitive information like inode number, multipart MIME boundary, and child process through Etag header. To prevent this vulnerability, lets implement it as below. This is required to fix for PCI compliance. Implementation Go to WebServerconf directory. Add the following directive and save the httpd. File. ETag None. Verification Open Firefox and access your application. Check HTTP response headers in firebug, you should not see Etag at all. Authorization. 3. Run Apache from non privileged account. Default apache configuration is to run as nobody or daemon. Its good to use a separate non privileged user for Apache. The idea here is to protect other services running in case of any security hole. Implementation Create a user and group called apachegroupadd apache. G apache apache. Change apache installation directory ownership to newly created non privileged user chown R apache apache optapache Go to WebServerconf Modify httpd. Search for User Group Directive and change as non privileged account apache. User apache. Group apache Save the httpd. Restart Apache. Verification grep for running http process and ensure its running with apache user ps ef grep http. Note You could see one process is running with root. Thats because Apache is listening on port 8. We will talk about how to change port number later in this course. Protect binary and configuration directory permission. By default, permission for binary and configuration is 7. You can disallow another user to get into conf and bin folder. Implementation Go to WebServer directory. Change permission of bin and conf folder chmod R 7. Verification 3. 3 System Settings Protection. In a default installation, users can override apache configuration using. Allow. Override to None as shown below. This must be done at the root level. Implementation Go to WebServerconf directory Open httpd. Search for Directory at root levellt Directory. Options Indexes. Allow. Override Nonelt Directory Save the httpd. Restart Apache. 3. HTTP Request Methods. HTTP 1. 1 protocol support many request methods which may not be required and some of them are having potential risk. Typically you may just need GET, HEAD, POST request methods in a web application, which can be configured in the respective Directory directive. Default apache configuration support OPTIONS, GET, HEAD, POST, PUT, DELETE, TRACE, CONNECT method in HTTP 1. Implementation Go to WebServerconf directory Open httpd. Search for Directory and add followinglt Limit. Except GET POST HEAD deny from alllt Limit. Except 4. Web Application Security. Apache web server misconfiguration or not hardened properly can exploit web application. Its critical to harden your web server configuration. Cookies. 4. 1. 1 Disable Trace HTTP Request. By default Trace method is enabled in Apache web server. Having this enabled can allow Cross Site Tracing attack and potentially giving an option to a hacker to steal cookie information. Lets see how it looks like in default configuration. Do a telnet web server IP with listening port Make a TRACE request as shown belowtelnet localhost 8. Trying 1. 27. 0. 0. Connected to localhost. Escape character is. TRACE HTTP1. 1 Host test. HTTP1. 1 2. 00 OK.
Following are tested on Apache 2. I dont see any reason it wont work with Apache 2. This assumes you have installed Apache on UNIX platform. If not, you can go through Installation guide. You can also refer very free video about how to Install Apache, My. SQL PHP. We will call Apache installation directory optapache as WebServer throughout this course. You are advised to take a backup of existing configuration file before any modification. Audience. This is designed for Middleware Administrator, Application Support, System Analyst, or anyone working or eager to learn Hardening Security guidelines. Fair knowledge of Apache Web Server UNIX command is mandatory. 2. Information Leakage. In default Apache configuration you would have much sensitive information disclosures, which can be used to prepare for an attack. Its one of the most critical tasks for an administrator to understand and secure them. As per report by Cenzic, 1. Info leakage. We require some tool to examine HTTP Headers for verification. Lets do this by install firebug add on in Firefox. Click on Install Now. Restart Firefox You can see firebug icon at right top bar. We will use this icon to open firebug console to view HTTP Headers information. There are many online tools also available which helps to check in HTTP header information. 2. Remove Server Version Banner. I would say this is one of the first things to consider, as you dont want to expose what web server version you are using. Exposing version means you are helping hacker to speedy the reconnaissance process. The default configuration will expose Apache Version and OS type as shown below. Implementation Go to WebServerconf folder. Modify httpd. conf by using vi editor. Add the following directive and save the httpd. Server. Tokens Prod. Server. Signature Off. Server. Signature will remove the version information from the page generated like 4. Server. Tokens will change Header to production only, i. Apache. Verification Open Firefox Activate firebug by clicking firebug icon at top right side Click on Net tab. Hit the URL in address bar. Expand the GET request and you could see Server directive is just showing Apache, which is much better than exposing version and OS type. Disable directory browser listing. Disable directory listing in a browser so the visitor doesnt see what all file and folders you have under root or subdirectory. Lets test how does it look like in default settings. Go to WebServerhtdocs directory. Create a folder and few files inside that mkdir test. Now, lets try to access Apache by http localhosttest. As you could see it reveals what all filefolders you have which are certainly you dont want to expose. Implementation Go to WebServerconf directory Open httpd. Search for Directory and change Options directive to None or Indexeslt Directory optapachehtdocs. Order allow,deny. Directory orlt Directory optapachehtdocs. Options Indexes. Order allow,deny. Directory Note if you have multiple Directory directives in your environment, you should consider doing the same for all. Verification Now, lets try to access Apache by http localhosttest. As you could see, it displays forbidden error instead showing test folder listing. Etag. It allows remote attackers to obtain sensitive information like inode number, multipart MIME boundary, and child process through Etag header. To prevent this vulnerability, lets implement it as below. This is required to fix for PCI compliance. Implementation Go to WebServerconf directory. Add the following directive and save the httpd. File. ETag None. Verification Open Firefox and access your application. Check HTTP response headers in firebug, you should not see Etag at all. Authorization. 3. Run Apache from non privileged account. Default apache configuration is to run as nobody or daemon. Its good to use a separate non privileged user for Apache. The idea here is to protect other services running in case of any security hole. Implementation Create a user and group called apachegroupadd apache. G apache apache. Change apache installation directory ownership to newly created non privileged user chown R apache apache optapache Go to WebServerconf Modify httpd. Search for User Group Directive and change as non privileged account apache. User apache. Group apache Save the httpd. Restart Apache. Verification grep for running http process and ensure its running with apache user ps ef grep http. Note You could see one process is running with root. Thats because Apache is listening on port 8. We will talk about how to change port number later in this course. Protect binary and configuration directory permission. By default, permission for binary and configuration is 7. You can disallow another user to get into conf and bin folder. Implementation Go to WebServer directory. Change permission of bin and conf folder chmod R 7. Verification 3. 3 System Settings Protection. In a default installation, users can override apache configuration using. Allow. Override to None as shown below. This must be done at the root level. Implementation Go to WebServerconf directory Open httpd. Search for Directory at root levellt Directory. Options Indexes. Allow. Override Nonelt Directory Save the httpd. Restart Apache. 3. HTTP Request Methods. HTTP 1. 1 protocol support many request methods which may not be required and some of them are having potential risk. Typically you may just need GET, HEAD, POST request methods in a web application, which can be configured in the respective Directory directive. Default apache configuration support OPTIONS, GET, HEAD, POST, PUT, DELETE, TRACE, CONNECT method in HTTP 1. Implementation Go to WebServerconf directory Open httpd. Search for Directory and add followinglt Limit. Except GET POST HEAD deny from alllt Limit. Except 4. Web Application Security. Apache web server misconfiguration or not hardened properly can exploit web application. Its critical to harden your web server configuration. Cookies. 4. 1. 1 Disable Trace HTTP Request. By default Trace method is enabled in Apache web server. Having this enabled can allow Cross Site Tracing attack and potentially giving an option to a hacker to steal cookie information. Lets see how it looks like in default configuration. Do a telnet web server IP with listening port Make a TRACE request as shown belowtelnet localhost 8. Trying 1. 27. 0. 0. Connected to localhost. Escape character is. TRACE HTTP1. 1 Host test. HTTP1. 1 2. 00 OK.